Run boosted AI agents.
Fearlessly.
DevCage doesn't just cage AI coding agents — it makes them better.
Hardened Docker containers with dropped capabilities,
network isolation, and zero-trust defaults protect your system. An enhanced system prompt gives every agent structured
work cycles, security-first patterns, and a mandatory definition-of-done checklist with a comprehensive toolset ready to be used.
Safer for you. Smarter for them.
Download DevCage v0.9.0
Windows or macOS with Docker Desktop recommended.
No admin privileges required.
Windows
Windows 10 or 11
One-click installer. Adds devcage to PATH and Explorer context menu integration.
macOS
macOS 10.15+ (Catalina or later)
Drag-and-drop installer. Adds devcage to PATH and Finder Quick Actions.
Portable
Windows 10+ / macOS 10.15+ / Linux
Extract and run ./devcage.sh or devcage.bat from any directory.
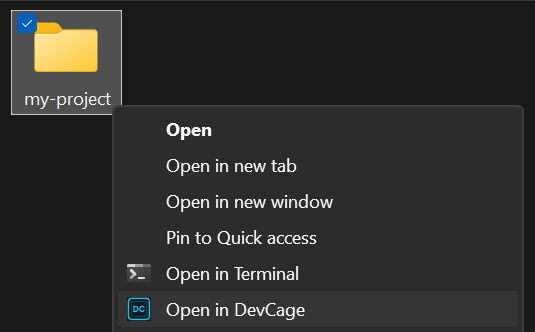
Right-click any folder.
Launch instantly.
The Windows installer adds Open in DevCage directly to Explorer's context menu. No terminal, no typing — right-click a project folder and you're inside a hardened sandbox in seconds.
Quick start in three steps
No global installs, no admin privileges, no configuration files to write.
Install
Prerequisites
Install Docker Desktop or Podman Desktop.
DevCage itself
Then download and install DevCage.
Launch an agent
Pick any AI agent. It will be installed automatically on first use.
Customize
Pin versions, set resource limits, enable GPU, or add packages.
Many agents. One sandbox.
Switch between AI coding tools instantly. Each is lazily installed on first use — no image bloat, no waiting.
Claude Code
Anthropic's agentic coding tool. Full terminal access, file editing, and git operations — safely contained.
Gemini CLI
Google's AI assistant for the command line. Code generation, explanation, and debugging — fully isolated.
Codex CLI
OpenAI's coding agent with autonomous task execution. Sandboxed so it can't touch your host system.
Aider
AI pair programming in the terminal. Supports multiple LLM backends with git-aware editing — all sandboxed.
Why sandboxing matters
AI coding agents need deep access to work — file I/O, shell execution, network calls, package installs. That power is exactly what makes running them on bare metal dangerous.
When you launch an AI agent on your workstation, you hand it your user-level privileges: every file you can read, every host you can reach, every credential stored in your profile. The agent doesn't need to be malicious — a single hallucination, prompt injection, or compromised dependency is enough to cause real damage. Sandboxing is not optional — it's a baseline.
File & Credential Protection
An unsandboxed AI agent can read far beyond your project: credentials, API tokens, private keys, and personal files. DevCage restricts the agent's view to your project directory — nothing else. Your secrets and other projects remain invisible.
LAN & Internal Network Defense
Your workstation sits inside the home or corporate network. A compromised agent could probe routers, NASes, internal services, access databases, or exfiltrate source code — all from a trusted machine. DevCage blocks all LAN traffic while keeping internet access for legitimate needs. Your internal network stays unreachable.
Hallucination Containment
AI agents don't just give wrong answers — they take wrong actions with full confidence.
A hallucinating agent might delete files, overwrite configs, or run destructive commands.
On bare metal, the blast radius is your entire machine. Inside DevCage, the worst case is a corrupted workspace
you can git reset. Your OS, other projects, and system configuration remain untouched.
Supply Chain Attack Mitigation
AI agents routinely install packages — creating a direct vector for supply chain attacks: typosquatted packages, compromised accounts, malicious install scripts. On bare metal, a rogue package runs with your full privileges. Inside DevCage, malicious code is contained in an isolated environment — it cannot access the host, reach the local network, or escape.
Container security model
Your code runs in an unprivileged workspace. Docker commands go through an isolated sidecar — never through the host socket.
dev tools, your code
TLS isolated
Engine detection
Launcher detects Docker or falls back to Podman automatically.
Container startup
Workspace and DinD sidecar spin up with resource limits and UID matching.
Security hardening
All Linux capabilities are dropped, iptables blocks LAN traffic, and agent configs are overlay-copied from read-only mounts.
Privilege drop
setpriv drops to unprivileged devcage user with no capabilities.
Agent launch
Your chosen AI agent starts in the secured workspace with full tool access.
Built for security-conscious developers
Every default is a secure default. GPU passthrough, cross-platform support, and professional dev tools included.
Defense in Depth
All Linux capabilities dropped. Temporary init caps permanently cleared via setpriv before any user code runs. No-new-privileges enforced.
Network Isolation
LAN traffic blocked via iptables so agents can't reach your local network. Full internet access is preserved for package installs, API calls, and git operations.
GPU Passthrough
Auto-detected NVIDIA and AMD GPU support via compose overlays. No configuration needed.
Cross-Platform
Native launchers for macOS, Linux, and Windows. Finder Quick Actions and Explorer context menus.
Docker-in-Docker
Agents can build images, run containers, and compose multi-service apps autonomously — through a TLS-isolated DinD sidecar, never the host socket.
Version Pinning
Pin exact tool versions in versions.conf for reproducible builds. Mixed pinned + latest supported.
Lazy Installation
AI tools installed on first use via wrapper scripts. Small base image, fast builds.
Config Protection
Agent configs are mounted read-only by default and overlay-copied into the container. Write access is opt-in.
Package Caching
Named Docker volumes persist Maven, npm, pip, Cargo, Go, and Gradle caches across sessions.
Seven layers of defense
Security isolation between your host and the AI agent, active by default.
Container Boundary
Workloads run inside Docker with no direct host access
Capability Dropping
cap_drop: ALL — temporary init caps cleared by setpriv on privilege drop
Privilege Restriction
no-new-privileges prevents any escalation
Unprivileged User
devcage user with host-matched UID, never root
Network Isolation
iptables blocks LAN traffic; internet stays open
Config Protection
Agent config dirs mounted read-only by default
Socket Isolation
Host Docker socket never mounted; TLS DinD sidecar used
Verify with one command
Built-in audit commands scan your project dependencies and the sandbox itself — no setup, no configuration.
Project Audit
audit
Scans your project for dependency vulnerabilities, code security issues, and committed secrets. Auto-detects package managers and runs the right checks.
$ audit --fix # auto-fix where possible
$ audit --level critical
$ audit --no-semgrep ~/myapp
Sandbox Audit
audit-sandbox
Verifies that the sandbox itself is properly hardened.
$ audit-sandbox --level critical
$ audit-sandbox --no-trivy
Batteries included
Ubuntu base with multiple programming language runtimes, all major package managers, and professional-grade tools — everything an AI agent needs to build, test, and ship software.
Languages & Runtimes
Package Managers
Semgrep
Static analysis security scanner. Find vulnerabilities, enforce code patterns, and run custom rules across 30+ languages. Catches OWASP Top 10 issues before they ship.
Trivy
Scan containers, filesystems, and dependencies for known CVEs. Generate SBOMs, check license compliance, and detect misconfigurations in Dockerfiles and IaC templates.
Playwright + Chromium
Full browser automation with real Chromium pre-installed. Run E2E tests, take screenshots, validate UI rendering across viewports, and interact with pages programmatically.
Lighthouse
Audit web pages for performance, accessibility, SEO, and best practices. Generate scores with actionable recommendations to optimize Core Web Vitals and WCAG compliance.
wrk
HTTP load testing and benchmarking. Measure request throughput, latency percentiles, and connection handling under sustained concurrent load.
Mailpit
Local SMTP server that captures all outgoing email. Web UI for inspecting messages, testing email workflows, and validating templates — without sending real mail.
Agents are smarter inside the cage
Every agent receives an enhanced system prompt — a full development methodology with first principles, structured work cycles, anti-pattern tables, and a definition-of-done checklist.
It turns AI agents from unreliable code generators into disciplined software engineering assistants.
Disciplined work cycle
Agents follow a structured loop: understand, baseline, change, verify, review, iterate. Tests run before and after every change — not just at the end. Three failed attempts trigger a step-back and re-analysis.
Security-first by default
Proactive security scans after every dependency change. Parameterized queries enforced, hardcoded secrets rejected, input validated at API boundaries. Agents know the OWASP Top 10 wrong/right patterns by heart.
Measure, don't guess
Playwright screenshots before and after every UI change at multiple viewports. Lighthouse for performance and accessibility scoring. wrk for API load testing. Visual regressions and performance issues are caught, not shipped.
Production-grade patterns
Connection pooling, N+1 query prevention, proper HTTP status codes, structured logging, dependency isolation, atomic git commits. Agents are taught concrete wrong/right examples for every common mistake — from SQL injection to swallowed errors.
Real services, not mocks
The DinD sidecar gives agents PostgreSQL, Redis, MongoDB, and MySQL on demand. Integration tests run against real databases with proper migrations — not in-memory fakes that mask production bugs.
Definition of Done
A mandatory checklist before claiming work is complete: tests pass, linter clean, security scanned, screenshots taken, git diff reviewed, no debug statements, every requirement addressed. "Should work" is not verification.
Four files, full control
Customize defaults, pin versions, and run startup scripts. All config lives on the host, never cached in the Docker image.
Persistent Defaults
Set memory limits, CPU count, default ports, and flags. CLI arguments override these. Key=value format.
Version Pinning
Pin Node.js, Java, Go, Rust, .NET, and 30+ tools to exact versions for reproducible builds. Rebuild after changes.
Startup Script
Environment variables, aliases, and custom setup. Sourced at container startup before running commands.
Environment Variables
KEY=VALUE pairs injected into the sandbox container. CLI --env flags take precedence over values here.
CLI flags at a glance
Every option has a sensible default. Override only what you need.
Simple Pricing
Build and contribute freely.
- All features included
- All supported AI agents
- For non-commercial use only
- Community support
- Your peace of mind and faster development
Billed annually at 48€.
- All features included
- All supported AI agents
- Unlimited usage
- Prioritized support
- Prioritized bug fixes
- Prioritized feature requests
- Funds active development and faster releases
- Your business continuity and secure apps